BitLocker is a security feature for Windows that offers volume encryption, protecting data from exposure or theft from misplaced, stolen, or improperly decommissioned devices. Read below about the BitLocker technology uses and how one can turn-on and turn-off the security and what major uses of BitLocker encryption. BitLocker is meant to keep computers and hard drives safe from hackers and other people who might try to access your data. Some of the major benefits are The TPM module gives it a high level of protection by encrypting your whole drive. BitLocker can be set up to save keys to Active Directory on its own.
Main BitLocker Technology Uses – It is a Useful applications
Unauthorized access to data on a lost or stolen device can occur through the use of software attack tools or through the transfer of the hard drive to an other device. By strengthening file and system security and making data unreadable when BitLocker-protected devices are recycled or retired, BitLocker technology uses helps reduce the risk of unwanted data access.
TPM and BitLocker
When combined with a Trusted Platform Module (TPM), a popular piece of hardware that is placed on Windows machines, BitLocker technology uses the highest level of safety. To make sure a device hasn’t been tampered with while the system is offline, the TPM collaborates with BitLocker.
BitLocker can lock the standard starting procedure in addition to the TPM until the user enters a personal identification number (PIN) or inserts a removable device that has a startup key. These security features ensure that the device cannot start or wake from hibernation unless the proper PIN or startup key is entered. They also offer multifactor authentication.
BitLocker can still be used to encrypt the operating system drive on systems without a TPM. With this implementation, the user must either:
- When resuming from hibernation, use the startup key, which is a file kept on a portable drive that is used to start the device.
- Put a password to use. This option lacks a password lockout logic, making it vulnerable to brute force assaults. Therefore, by default, the password option is deactivated and discouraged.
The preboot system integrity verification that BitLocker technology uses with a TPM offers is not available with either option.
Check BitLocker preboot – Computer screen with startup key:
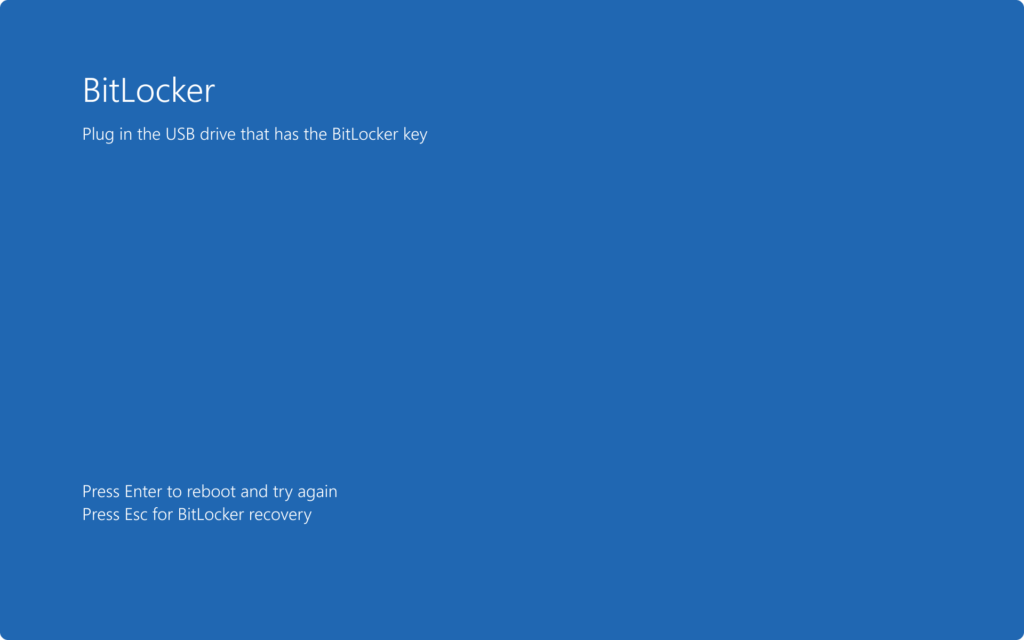
Check – BitLocker preboot – Computer screen with PIN:
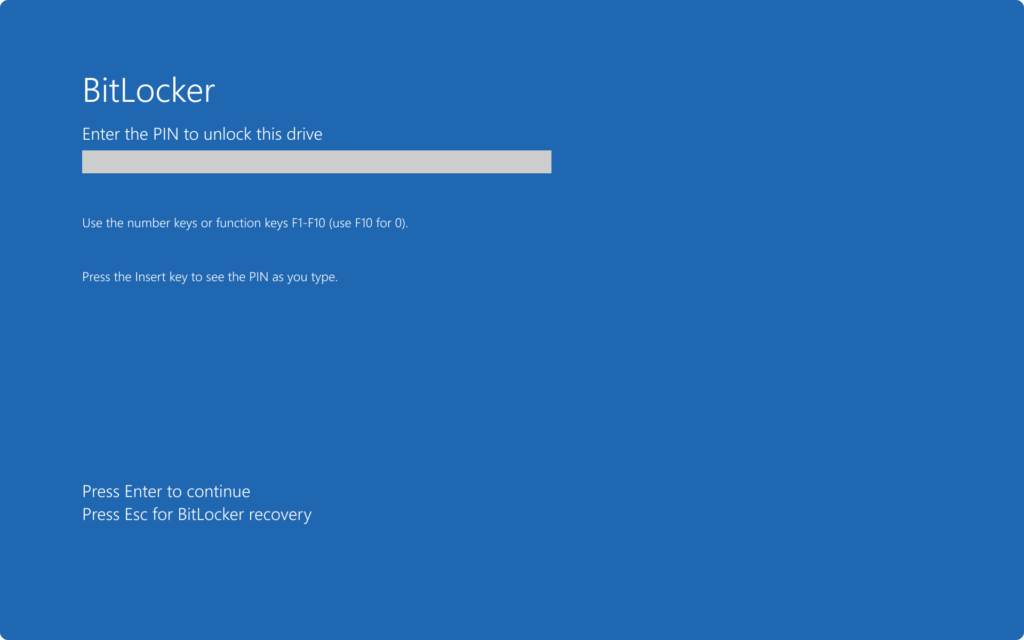
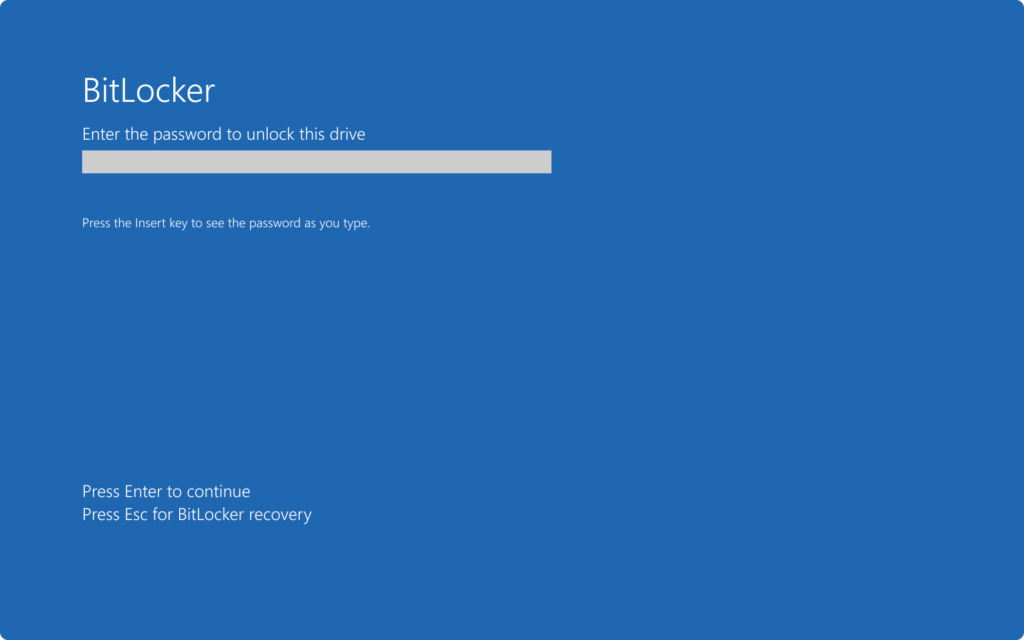
Check the BitLocker preboot Computer screen with password:
System prerequisites
The prerequisites for BitLocker are as follows:
- The device must have TPM 1.2 or later versions in order for BitLocker technology uses the system integrity check that a TPM provides. Enabling BitLocker requires storing a startup key on a portable drive if the device lacks a TPM.
- In addition to having a TPM, a device’s BIOS or UEFI software needs to be compliant with the Trusted Computing Group (TCG). For the preboot startup, a chain of trust is established by the BIOS or UEFI firmware, and it needs to implement the TCG-specified Static Root of Trust Measurement. Firmware compliant with the TCG is not necessary for a computer lacking a TPM.
- The USB mass storage device class and the ability to read files from a USB drive in the preboot environment must be supported by the system BIOS or UEFI firmware (for TPM and non-TPM devices).
Take note
The BIOS’s Legacy and Compatibility Support Module (CSM) modes do not support TPM 2.0. The BIOS mode of devices equipped with TPM 2.0 must be set to native UEFI exclusively. Disabling the Legacy and CSM settings is necessary. Turn on secure boot for further security.
When the BIOS mode is changed to UEFI, an operating system that has been installed on hardware in Legacy mode prevents the OS from booting. Before altering the BIOS mode, use the program mbr2gpt.exe to get the OS and the disk ready to handle UEFI.
At least two disks must be used to partition the hard drive:
- The OS and its support files are located on the boot drive, also known as the operating system drive. It has to have the NTFS file system formatted.
- The files needed to boot, decrypt, and load the operating system are on the system drive. There is no BitLocker enabled on this drive. BitLocker technology uses the following to function:
- It can’t be encrypted
- ought to be distinct from the operating system disk.
- needs to be formatted using the NTFS file system on computers running BIOS firmware or the FAT32 file system on machines using UEFI-based firmware.
- It is advised that the file be roughly 350 MB in size. BitLocker technology uses about 250 MB of free space after it is turned on.
Important
Windows makes the necessary partitions for BitLocker when it is installed on a new device.
In order to store the boot files, BitLocker needs a new volume if the drive was formatted as a single, continuous area. The volume can be created via BdeHdCfg.exe. Refer to Bdehdcfg in the Command-Line Reference for further details on how to use the program.
Take note
The Enhanced Storage feature needs to be installed on a server before installing the BitLocker optional component. Drives that are hardware encrypted are supported by this capability.
Requirements for Windows edition and licensing
The Windows editions that allow BitLocker enablement are listed in the following table:
Windows Editions:
- Pro – Yes
- Enterprise – Yes
- Pro Education/SE – Yes
- Windows Education – Yes
BitLocker enabled license rights are given out by the following licenses:
- Pro/Pro Education/SE- Yes
- Windows Enterprise E3 – Yes
- Windows Enterprise E5 – Yes
- Windows Education A3 – Yes
- Windows Education A5 – Yes
Check out Windows licensing summary to learn more about how to license Windows.
Note: One type of licensing is needed to allow BitLocker, while another type is needed to manage BitLocker. Read the how-to guide to find out more: set up BitLocker.
Encrypting the device
Device encryption is a function of Windows that makes it easy for some devices to automatically use BitLocker encryption. Device encryption works with all versions of Windows, but the device needs to meet either Modern Standby or HSTI security standards. Encrypted devices can’t have DMA ports that can be accessed from the outside.
Very Important: Device encryption only protects the OS drive and fixed drives; it doesn’t protect USB or external disks.
In contrast to a normal BitLocker setup, device encryption is turned on by default, which means the device is always safe. After a fresh installation of Windows and the out-of-box experience, the gadget is ready to be used for the first time. To get ready, device encryption is set up on the computer’s OS drive and fixed data drives with a clear key, which is the same as BitLocker technology uses being in a normal paused state. In this state, Windows Explorer shows the drive with a warning sign. After the TPM guardian is set up and the recovery key is backed up, the yellow warning icon is taken away.
- On devices that are joined to Microsoft Entra or Active Directory, the clear key is taken away once the recovery key has been safely backed up to Microsoft Entra ID or Active Directory Domain Services (AD DS). For the restore key to be backed up, the following policy settings must be turned on: Pick how to get back operating system files that are protected by BitLocker.
- For Microsoft Entra joined devices, the recovery password is made immediately when the user logs in with their Microsoft Entra ID. The recovery key is then backed up to their Microsoft Entra ID, the TPM protector is made, and the clear key is taken away.
- For devices that are joined to AD DS, the recovery password is made for them immediately when they join the domain. After that, the recovery key is saved to AD DS, the TPM guardian is made, and the clear key is taken away.
- You need a Microsoft account with management rights on the device if it isn’t already joined to Microsoft Entra or an Active Directory domain. The clear key is taken away, a recovery key is sent to the administrator’s online Microsoft account, and a TPM defender is made when the administrator signs in with a Microsoft account. Should a device need the recovery key, the user is told to use a different device and go to a recovery key access URL with their Microsoft account information to get the key.
- Even if the data on a device is secured, it is not safe if it only uses local accounts.
Very Important
By default, XTS-AES 128-bit encryption is used for device security. You can use the Enrollment Status Page to stop the device from starting to encrypt with the usual method if you set up a policy setting to use a different one. BitLocker doesn’t start encrypting until the end of OOBE, which means that it starts after the Enrollment Status Page device configuration process is over. It gives the device enough time to get the BitLocker policy options before it starts encrypting.
If you need to use a different encryption method or cipher strength on a device that is already protected, you must first decrypt it. Only then can you use the new method or strength. You can change BitLocker settings after the device has been unlocked.
If you make a change to a device that makes it eligible for device encryption, like putting on Secure Boot, and then the device doesn’t qualify at first, device encryption turns it on automatically as soon as it finds it.
The System Information app (msinfo32.exe) lets you see if a device meets the standards for device encryption. It has to meet certain conditions before System Information shows a line that says:
BitLocker is not the same as hardware encryption.
- With device encryption, BitLocker technology uses instantly turned on for devices that qualify. The recovery key is then saved in Microsoft Entra ID, AD DS, or the user’s Microsoft account.
- Making the Settings app have a device encryption setting is what device encryption does. This setting can be used to turn device encryption on or off.
The Settings menu doesn’t show that device encryption is on until it’s done.
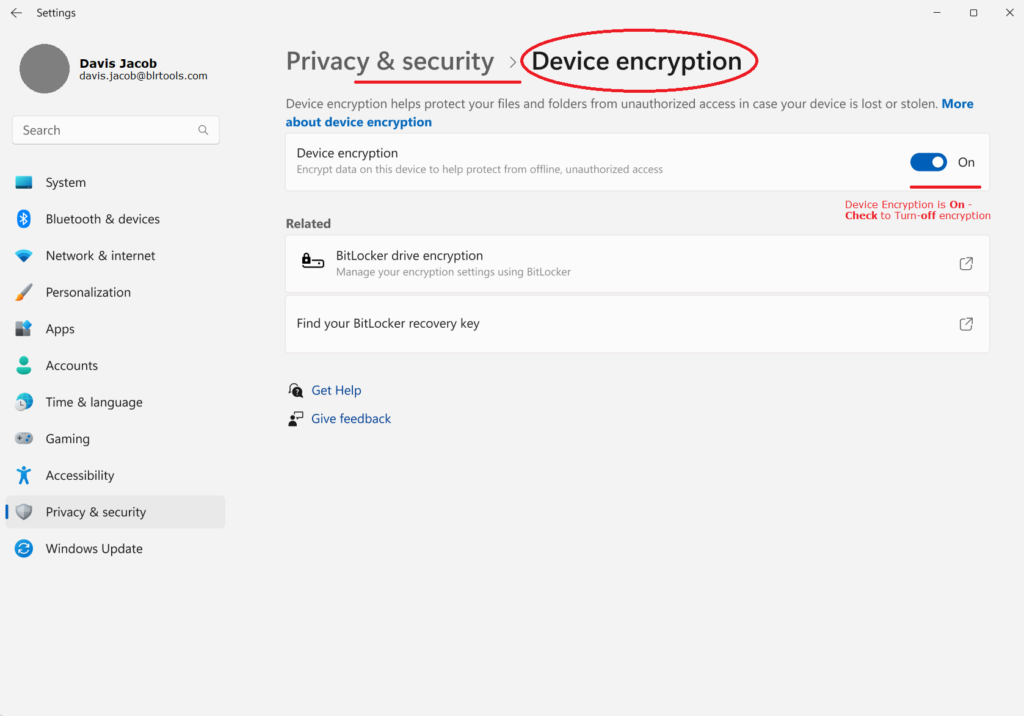
Note: If encryption is turned off on a device, it will not turn it on by itself in the future. The person has to turn it on by hand in Settings.
Turn off device security
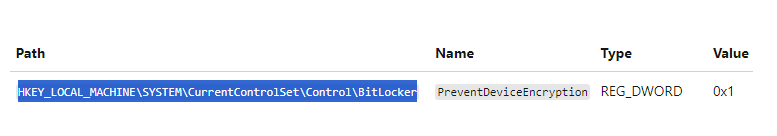
Device encryption should be left on for any computers that can handle it. You can stop the regular encryption of your device, though, by changing the following registry setting:
Read also relevant articles:
Automatic BitLocker Encryption on Windows Dell PC

1 Comment